For the company: fraudsters have become more likely to disguise phishing as employer services
- Статьи
- Society
- For the company: fraudsters have become more likely to disguise phishing as employer services

Cyberfraudsters have become more frequent in disguising phishing links as checks of employer services - to access the infrastructure of various organizations. This was reported to Izvestia by information security companies. For example, employees are asked to enter a special site under their login and password and test the functioning of the remote access service, confirm or change their credentials. And about 45% of users enter them. Moreover, similar mailings are being made from hacked addresses of the firms' partners.
Send from a link
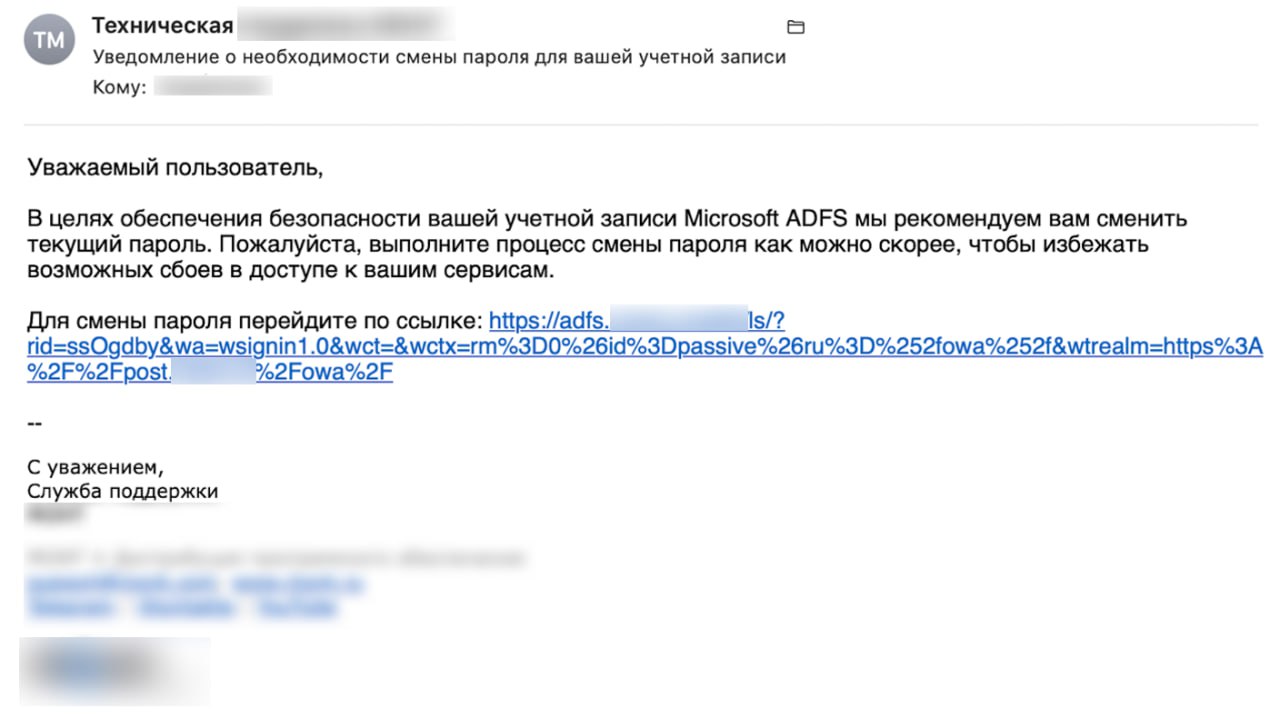
The mechanism of fraudulent mailings, which look like internal emails of organizations, became especially popular with attackers in late 2024 and early 2025. This was reported to Izvestia by information security companies. To gain access to the infrastructure of a firm, attackers design the letter as a request to employees to check this or that service or as a requirement to confirm or change the password.
"We are writing to inform you that due to recent changes in the company's access system, you need to go through an authorization procedure to verify access to resources," reads, for example, one of the emails from a fake employer. - Go to the authorization server using the link, enter your credentials (login and password), select the necessary resource from the list, make sure it works properly".
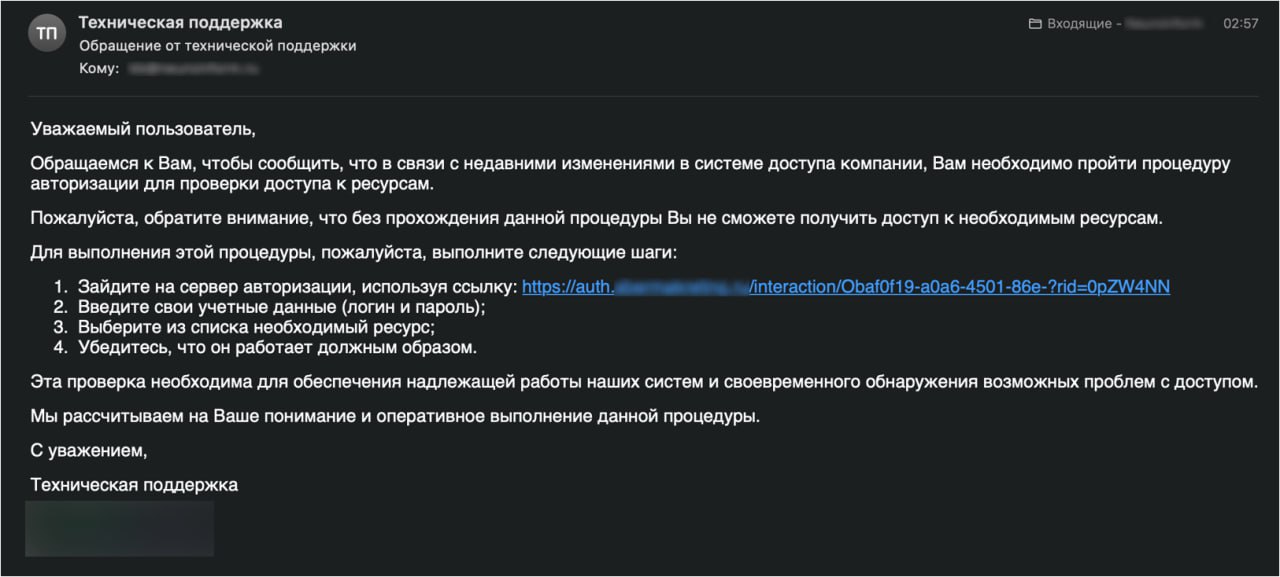
The "technical support team" goes on to say that it "expects understanding and prompt completion of this procedure."
Companies from the financial sector, retail, logistics, manufacturing and telecom have been subjected to such attacks over the past two months, Alexander Dmitriev, general director of the information security company Neuroinform, told Izvestia.
- In total in December there were 18 companies among our clients who were sent such letters, and from January 1 to January 20 - 12 more, - he said.
Alexander Dmitriev also cited a specific case of one of his clients (the name of the company cannot be disclosed because of the confidentiality agreement). It is a retail company.
At first, the attackers identified the possibility to pick up e-mail addresses of the company's employees. To do this, they picked up the names of users registered in the organization's system. If the user existed, a captcha appeared after entering an incorrect password. And if the supposed username did not exist, the captcha did not appear. Based on this system error, the fraudsters picked 50 accounts, figured out their email addresses, and sent phishing emails to employees.
- One of the employees who entered his username and password had permission to connect to a remote desktop. Attackers went to the mail, found a letter from tech support describing how to connect to VPN, and thus got into the internal network of the company, - said Alexander Dmitriev.
Then, taking advantage of flaws in the domain controller settings, the cybercriminals obtained domain administrator rights. About two weeks after the phishing mailing, all data was encrypted.
However, this company had a system backup on remote servers that was not accessed under a domain account. So after a week, the data was restored, but even though there was a backup, it took about a month to fully restore all systems.
- And it will take about another six months to remake the infrastructure and close the discovered vulnerabilities," the expert said.
According to Neuroinform, after receiving requests from the "technical team" to use one or another service of the company, 60% of employees click on such links, and 45% of those who clicked enter their corporate data.
How fraudsters' approaches are changing
The most common ways of attacking companies are phishing and emails with malicious attachments, Viktor Ievlev, head of the information security department of the Garda group of companies, reminded Izvestia.
But at the same time the text of the letter, which should induce an employee of the organization to go to a fake resource or open a file with "malware", is always changing, said Dina Fomicheva, head of the corporate clients department of the IT integrator "Telecom Exchange".
- It can be a photo from a New Year's corporate party, a link to a new provision on bonuses, even a postcard for March 8, letters from government agencies," she said.
Messages from employers most people perceive as a work assignment, which must necessarily fulfill, noted in "Neuroinform".
"In this case, attackers use the employees' sense of responsibility, as well as their desire to work as efficiently as possible. Often in the letter fraudsters scare the consequences - up to the deprivation of bonuses, if the employee will not react to the letter," - warned cybersecurity experts.
As Dina Fomicheva noted, such mailings are a relatively simple attack, and with proper configuration of the mail server and the necessary training in the company, the risks of opening such letters can be minimized.
- It is more difficult to resist attacks when a counterparty's mail is hacked and messages are sent through it," the expert said. - A real case in point is when attackers hacked into a water supplier and got into the infrastructure of a large company through him.
To prevent attackers from gaining access to the organization's infrastructure, information security services need to conduct ongoing training of employees, test phishing attacks and testing for knowledge of the basics of information security, reminded Viktor Ievlev.
- It is necessary to check the settings set by IT departments, control the rules on firewall, conduct vulnerability scans both within the local network and on the perimeter and external services of the company, - he said.
Also, according to him, any company should involve third-party organizations to conduct pentest (a set of measures that simulate a real attack on the system or network) to make sure that nothing was missed when building a protection system.
Alexander Dmitriev recommended that companies install specialized software that checks the content of emails for viruses, links to suspicious resources, and regularly hold classes to raise employee awareness of cyber threats. Usually, this is a set of activities that include seminars to review pseudo-phishing mailings and identify employees who succumbed to provocations, followed by explanations of mistakes and possible consequences for both the company and the employee personally.
In addition, the expert urged companies not to neglect multi-factor authorization. In this case, even if an employee enters his or her credentials on a phishing site, the attacker will not be able to use them, as he or she will be asked to enter an additional one-time password.
Переведено сервисом «Яндекс Переводчик»

